©threatER 2024
What Threater Enforce Does
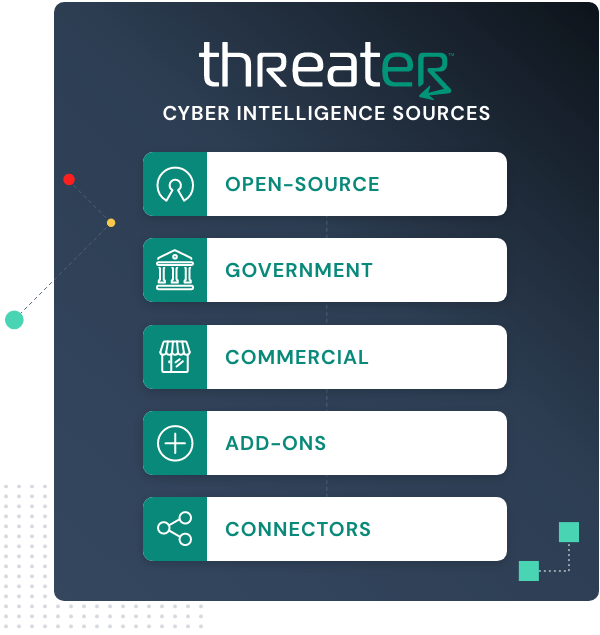
Aggregates
Easily gain access to the world’s best third party cyber intelligence and services by utilizing the Threater Cyber Marketplace in addition to your own feeds and data sources to inform your blocking parameters.
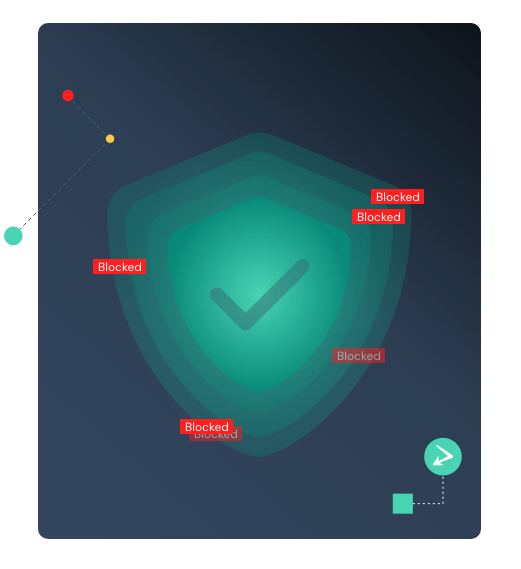
Blocks
Harness unmatched amounts of cyber intelligence to autonomously block known threat actors coming in and out of the network at line speed.
Enhances
Reduce network traffic and arm your team and other technologies with powerful insights about what is happening in your network in real time.
Foundational Network Security
Aggregate best-in-class cyber intelligence
Enforce focuses on who is sending the threats instead of the threats themselves.
Modern day threat actors are nimble and adapt their code quickly to evade detection. But as the methods and types of attacks constantly evolve, the constant in the cybersecurity equation is the “who”: threat actors themselves, not the “what” of the attacks.
Enforce aggregates best-in-class cyber intelligence feeds to inform enforcement decisions seamlessly on both inbound and outbound traffic.
Instead of relying on a single vendor’s view of the threat landscape, Enforce leverages the full power of the cyber intelligence community to inform blocking decisions and stop communications with known threat actors, no matter how they enter or exit the network.
Enforce can ingest and enforce on up to 150 million threat indicators at line speed and updates automatically.
Because Enforce does not rely on a single proprietary view of the threat landscape, it can ingest as much cyber intelligence as is available today in order to block traffic based on the best and most up-to-the-minute intelligence available.
Block known threat actors at the network level autonomously
Informed by best-in-class cyber intelligence, Enforce blocks traffic to and from known threat actors.
No matter how threat actors are trying to get in, Enforce stops the call. This results in removing up to 30-50% of network traffic hitting your firewall and security stack.
And because of Enforce’s patented technology, enforcement happens at line speed with no impact to network performance, all without the need for monitoring by employees.
Users can also adjust their risk threshold limits for various types of malicious traffic, sourced from cyber intelligence feeds. These can be customized for inbound vs. outbound traffic, all handled with ease in the Enforce platform.
Enhance your security team and technologies
The internet is a hostile environment. Threat actors are not only sending large amounts of encrypted traffic but also using “back door” entrances to the network such as stolen passwords, phishing, and other means.
Right now security teams and technologies are bogged down with redundant alerts and unnecessary triaging of known-bad traffic.
By removing this traffic going to and from known threat actors, Enforce eliminates up to 30-50% of internet traffic. This allows your teams and technologies to focus on the unknown instead of wasting their time and resources on known-bad traffic.